Solutions
Cybersecurity Solutions
Table of Contents
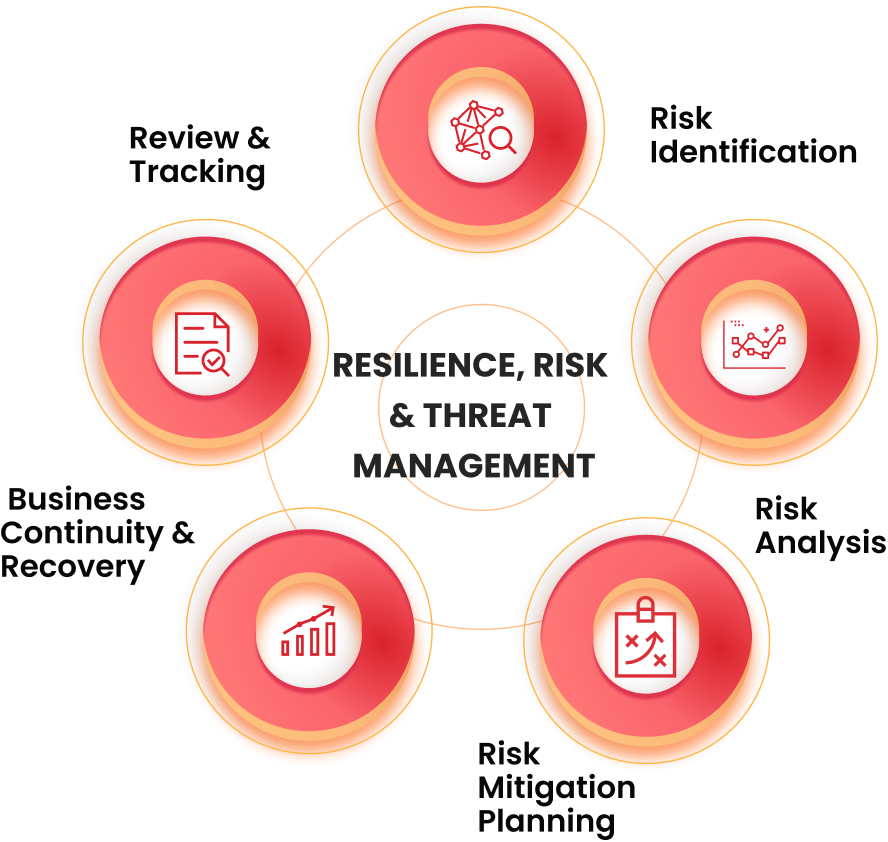
Resilience, Risk & Threat Management
Build a resilient cyber defense with our comprehensive Risk & Threat Management solutions. We identify vulnerabilities, assess risks, and implement proactive strategies to fortify your digital landscape against evolving threats, ensuring business continuity.

InfoSec & Security Operations Center (SOC)
Safeguard your information assets with our InfoSec solutions, backed by a state-of-the-art Security Operations Center (SOC). Our SOC experts provide 24/7 monitoring, threat detection, and rapid incident response to keep your infrastructure secure from cyberattacks.

Data Security
Protect your sensitive information with robust Data Security strategies. From encryption to secure data transfer, our solutions ensure that your data remains protected throughout its lifecycle, safeguarding it from unauthorized access and breaches.
Application Security & Cloud Security
Secure your digital applications and cloud environments with our advanced security protocols. We employ cutting-edge techniques to identify vulnerabilities, mitigate risks, and ensure your software and cloud platforms are secure from internal and external threats.
OT & IoT Security
Shield your Operational Technology (OT) and IoT ecosystems from cyber risks with our specialized security solutions. We design tailored protection strategies that secure connected devices, industrial systems, and smart infrastructure against potential cyber threats.

Identity & Access Management (IAM)
Enhance security with our Identity & Access Management solutions that ensure only the right individuals have access to your critical systems. Our IAM framework provides multi-factor authentication, role-based access, and comprehensive control over user identities.

Cohesive Posture Management
Achieve a unified security posture with our cohesive management strategies that integrate tools, policies, and procedures. We help you maintain a consistent security framework across your enterprise, reducing gaps and enhancing your overall cyber resilience.

Governance, Risk & Compliance (GRC)
Navigate regulatory landscapes with ease using our Governance, Risk & Compliance (GRC) solutions. We streamline compliance processes, reduce risks, and ensure your organization adheres to industry standards and legal requirements.

Cyber & Risk Analytics
Turn data into actionable insights with our Cyber & Risk Analytics solutions. We leverage advanced analytics to identify patterns, predict threats, and drive strategic decisions that enhance your cyber defenses and reduce risk exposure.

Third-Party Risk Management
Mitigate risks associated with third-party vendors through our comprehensive Third-Party Risk Management solutions. We assess, monitor, and manage vendor relationships to ensure that your supply chain remains secure and compliant.

Digital Forensics
Uncover and analyze digital evidence with precision through our Digital Forensics services. We help you identify the root cause of cyber incidents, gather critical evidence, and develop strategies to prevent future breaches.

Security Data Fabric
Integrate and streamline your security data with our innovative Security Data Fabric solutions. We create a unified data architecture that enhances visibility, accelerates threat detection, and enables faster, data-driven security responses.